Latest News

Photo: Via Satellite illustration
The U.S. Department of Homeland Security is deciding how to incorporate space assets like new multi-orbit constellations of broadband communications satellites into its efforts to protect the country’s vital national infrastructure, officials and executives tell Via Satellite.
Space capabilities will be a kind of guinea pig for a new approach to DHS’s mission to protect critical infrastructure by working with the private sector companies that own the infrastructure, according to Bob Kolasky, who runs the National Risk Management Center, part of DHS’ Cybersecurity and Infrastructure Security Agency.
Under congressional mandate, he said, DHS will “relatively shortly” lay out “a process by which we’re proposing reviewing and considering the sector structure.” Currently DHS outreach and partnership efforts with vital industries like banks and power companies is organized through 16 designated critical infrastructure sectors, like financial services, energy, and food and agriculture. Last year, in the annual defense policy legislation, Congress told the department to take a good look at that policy framework, which dates back to the Clinton administration, and see if it needs updating.
“Coincidentally,” Kolasky explained, “that review process will probably be first tested on space.”
Since its establishment in the wake of the 9/11 terror attacks, DHS has led the mission of hardening the operations of the nation’s key businesses — the 16 critical infrastructure sectors — against a range of natural and man-made threats.
Both new space-based systems, like IoT management technology or commercial Earth Observation (EO); and traditional satellite use cases like ubiquitous broadband communications are increasingly vital to a growing list of nationally significant industries — not to mention their role as commercial service providers to the military.
To address those new risks, Kolasky said, as DHS announced at CyberSat Digital in May, the department has established a Space Systems Critical Infrastructure Working Group consisting of representatives of the 13 federal agencies with space-related responsibilities; multiple businesses that own and operate space-related infrastructure, including launch and ground control systems; and other interested parties like academic associations, trade organizations, and federally-funded research centers.
Under special post-9/11 rules for critical infrastructure protection, the working group’s deliberations are not open to the public, as is generally mandatory for other kinds of panels and commissions that give a government advisory role to commercial interests. The working group’s membership list, for example, has never been published. It was released to Via Satellite by Kolasky and is It includes government agencies like the FCC and NASA, companies including Hughes Network Systems and Redwire, and organizations like American Institute of Aeronautics and Astronautics.
The working group was set up, Kolasky said, “to think through the question of how we treat space as critical infrastructure, [to figure out] where are the key risks that need national security attention, and to make sure that we had robust public private partnership between government and space infrastructure for the purposes of critical infrastructure security and resilience.”
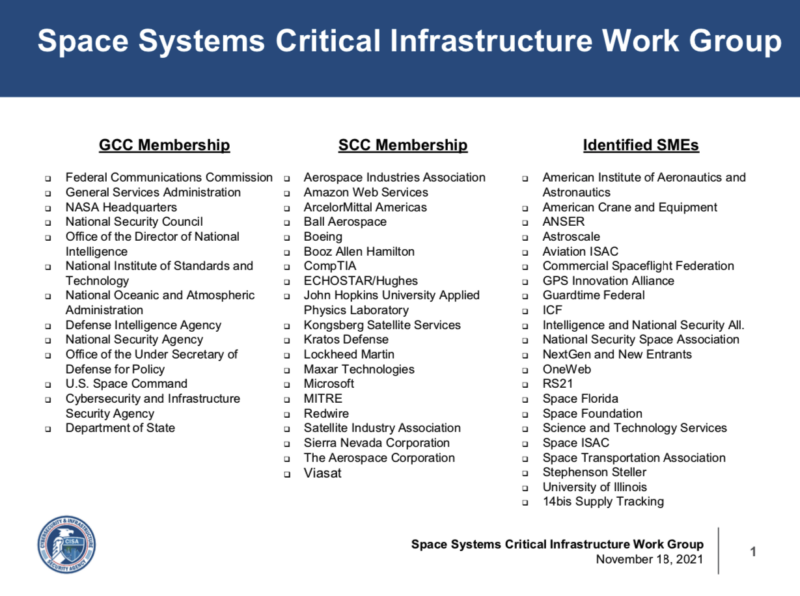
The DHS Space Systems Critical Infrastructure Working Group membership list.
To Designate or Not?
The space industry is not designated as an official critical infrastructure sector, but many in the industry have called for this to change. For more than two years, the Space Information Sharing and Analysis Center has been campaigning for space to be designated as the 17th sector. Space-ISAC is a non-profit set up to ensure that information about cyber and other security threats is shared among competing owners and operators of space-related systems.
The DHS working group only proves the need for the designation of space, said Space-ISAC Executive Director Erin Miller, who is a member of the working group.
“We’re regularly engaging on topics that are not being addressed in any other forum,” she said. “So that in and of itself proves out the model that this [risk to space-related infrastructure] is not being addressed by the other critical infrastructure sectors.”
“We need a single forum to address the management of risk to the space sector,” she concluded.
This month, that campaign got support from the Intelligence and National Security Alliance, a trade association that represents contractors selling to the U.S. intelligence community.
The Nov. 15 Russian test of an Anti-Satellite (ASAT) weapon demonstrates the very real threat adversaries can pose to U.S. space systems, noted Larry Hanauer, INSA vice president for policy.
“Designating space as a critical infrastructure sector would be good for the security and resiliency of space assets in a number of ways, but the principal advantage would be to enhance information sharing between private sector space companies and government organizations. So everyone in both government and industry can better understand and mitigate both physical and cyber threats,” he said.
So far, the Biden administration seems to have set its face against adding space as a 17th sector.
“There may be [industries] where you don’t need a sector designation — and this could be where we end up with space — you just need constant attention to understand the risks and make sure that the players who are the big drivers are mitigating those risks; that information sharing arrangements are in place; and that communications channels are open, and we are having regular dialogues,” said Kolasky.
He said all of those activities are being done by the working group. And he noted that many existing sectors are aware of their reliance on space-based capabilities — “The communication sector, the transportation sector, the defense industrial base, [and] critical manufacturing … There are many elements of space infrastructure that are accounted for in the existing sector structure,” he said.
The working group’s activities are still at a preliminary stage, explained co-chair John Galer, assistant vice president for national security space at the Aerospace Industries Association.
“We are still trying to figure out what our outputs look like,” he said, “And I would say we’re not 100 percent settled on that.”
He noted that it is important “to make sure that we are not duplicating any effort, but going after the areas where we can make a real impact. You cannot solve every problem. And so, we’ve got to really put the focus … on ideas that we think would bring some real goodness,” he said.
A New Approach
In any case, the question of whether space should become the 17th sector or not may be overtaken by changes in the department’s approach to its critical infrastructure protection mission, according to public comments by DHS and White House officials.
Officials like Chris Inglis, the national cyber director in the Biden White House see the sector-based approach as too stovepiped. A sector-based approach “leads us to a false conclusion,” he told CyberSatGov in October — the idea that each sector could be defended separately from the others. It was an illusion to think “that we can get one of those right in the absence of [getting] the other 15 right,” he said.
He pointed out that the most important risks, like extreme weather events or mass-effect terror attacks, for example, almost always impact multiple critical infrastructure sectors. And failures in one sector — energy and banking most obviously — can set off a cascade of failures across multiple sectors.
Inglis advocates for a more functions-based approach to critical infrastructure. Providing health care or financial services for instance, requires an interlocking grid of service providers across multiple sectors.
Kolasky said that assessing cross sector risk to critical functions — and looking at criticality as the point where multiple cross-sector risks collide — is a more useful approach. “We operated for a long time, on the understanding that entities were responsible to assess and manage the risk to their own operations. And that collectively, with that happening, we would address the [bigger systemic] risks.”
But in reality, no matter how good a hospital’s incident response plans are, if it is cut off from water, or internet connectivity or power, it will fail sooner or later.
A functions-based approach, “provides a better organization to work together to assess and manage risk to critical services,” said Kolasky.
Get the latest Via Satellite news!
Subscribe Now